DOS & DDOS Attack
Admin
10/8/20242 min read
A DoS attack can make a website or service unavailable to legitimate users, causing lost revenue and damage to customer relationships.
Sites may remain online during a DoS attack. They may become slow or unresponsive, making it difficult or impossible for users to interact.
The aftermath of a DoS attack can be expensive. Extensive damage can be done to the target, or legal fees may be incurred.
A successful DoS attack can damage a company’s reputation, especially if it results in extended downtime or data breaches.
Detecting a DoS attacks early is crucial in minimizing its impact. Indicators that a DoS attack may be underway include:
Abnormally high traffic
slow or unresponsive servers
High server utilization
Unusual traffic patterns
Unusual traffic sources
How can denial-of-service attacks be prevented?
Preventing a DoS attack can be challenging, but there are several effective techniques:
Network segmentation – Segmenting networks into smaller, more manageable pieces, can limit the impact of a DoS attack. This can be done by creating VLANs, and firewalls can limit the spread of an attack.
Load balancing – Distributing traffic across multiple servers, a DoS attack can be prevented from overwhelming a single server or resource. Load balancing can be achieved using hardware or software solutions.
IP blocking – Blocking traffic from known or suspected malicious sources can prevent DoS traffic from reaching its target. By checking the logs, you can get to know about the location/region and IP of attacker.
Content Delivery Networks (CDNs) – Distributing website content across multiple locations makes it more difficult for an attack to bring down an entire site.
There are also several tools, software’s & online services available to purchase, who can take care of prevention of several cyber-attacks and let you focus on your business. We are not naming them as we are not advertising them 🙂
Happy browsing…
Mivaayu Technologies
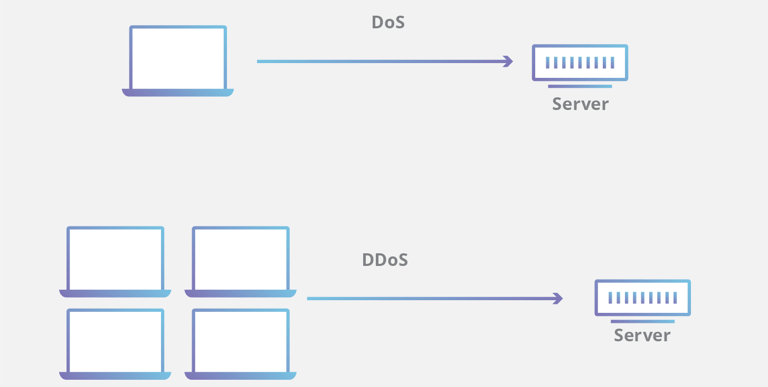
A denial-of-service (DoS) attacks typically function by overwhelming or flooding a target machine with thousands of requests until normal traffic unable to process or the machine ports unable to respond to the genuine queries, resulting in denial-of-service to addition users. A DoS attack is characterized by using a single computer to launch the attack.
A distributed denial-of-service (DDoS) attack is a type of DoS attack that comes from many distributed sources, such as a botnet DDoS attack.
DoS attacks typically fall in 2 categories:
Buffer overflow attacks ->
An attack type in which a memory buffer overflow can cause a machine to consume all available hard disk space, memory, or CPU time. This form of exploit often results in sluggish behavior, system crashes, or other deleterious server behaviors, resulting in denial-of-service.
Flood attacks ->
By saturating a targeted server with an overwhelming amount of packets, a malicious actor is able to oversaturate server capacity, resulting in denial-of-service. In order for most DoS flood attacks to be successful, the malicious actor must have more available bandwidth than the target.